Introduction
Most administrators simply update their virtual machines with the version of VMware Tools that comes with the ESXi build. As of a few years ago, VMware bifurcated VMware Tools into multiple streams. The article detailing this can be read here. As a result, some versions of VMware Tools are release outside of the ESXi patch cycle. To make those releases available on hosts for installation on virtual machines (VMs), a new procedure needs to be used. The purpose of this document is to provide guidance on how to handle an update of VMware Tools on ESXi hosts. This guide is specific to version 6.x.
Process Summary
- Identify the VMware Tools Builds in the environment
- Confirm whether the version in place can be upgraded directly to the desired version
- Download the VMware Tools VIB for the version desired
- Upload VMware Tools Offline Bundle to Update Manager update store
- Create new update baseline in vCenter/Update Manager for new VMware Tools version
- Use baseline to push new VMware Tools version to ESXi hosts
- Use Update Manger to update VMware Tools to on VMs
- Validate the tools version is correct
Details and Scope of VMSA-2021-0013 & VMSA-2021-0011
Summarizing VMSA 2021-0013 and 2021-0011, all Windows VMs need VMware Tools updated to version 11.3.0 or later. There are other aspects to these VMSA, specifically VMRC and App Volumes, but they are out of scope for this document. VMs running Linux need not be addressed.
Mapping Build Number to Version
When viewing VMware Tools versions in vCenter, an administrator would typically look at the summary tab to view the version of an individual VM, as shown below.

Figure 1 – VMware Tools Build in Summary View
To view tools version in masse, select a cluster, click on VMs and ensure the VMware Tools Version Status field is listed.

Figure 2 – VMware Tools Build in Cluster View
In both cases, the VMware Tools build number shown is cryptic. Follow the link below to map build number to version
https://packages.vmware.com/tools/versions

Figure 3 – VMware Tools Build Number to Version Mapping
Determine Tools Upgradability
Once an inventory of the VMware Tools Versions exist, confirm the versions that are in place can be upgraded to the destination version. This can be done by viewing the VMware Product Interoperability Matrix – Upgrade Path here: https://interopmatrix.vmware.com/Upgrade?productId=139. In some cases, a multi-step upgrade may be necessary.
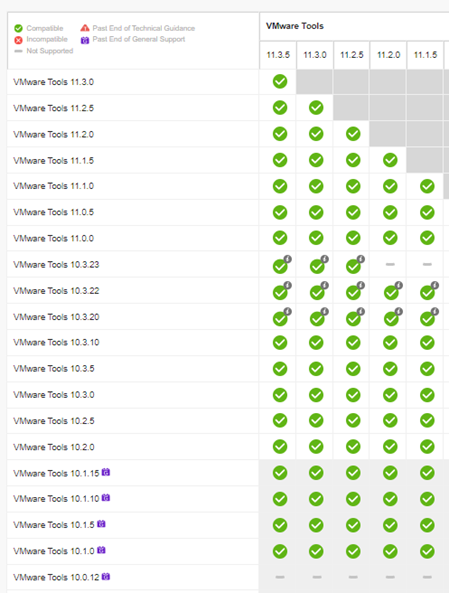
Figure 4 – VMware Tools Upgrade Path
Download VMware Tools
First, download
https://customerconnect.vmware.com/downloads/details?downloadGroup=VMTOOLS1130&productId=742

Figure 5 – VMware Tools Offline VIB Bundle Download
Create new update baseline in vCenter/Update Manager
One the VMware Tools Offline VIB Bundle has been downloaded, upload it to the Update Manager update repository. Navigate to Menu | Update Manager | Updates and choose Update From File.

Figure 6 – Upload Update to Repository from a File
Click Browse, select the zip file containing the VMware Tools Offline VIB Bundle and click Open. Then, click Import.

Figure 7 – Select the VMWare Tools Offline VIB Bundle
The bundle will begin importing. Observe and enjoy the progress.

Figure 8 – Import Progress of VMWare Tools Offline VIB Bundle
Once uploaded, create a new baseline in Update Manager. Go to Baselines, click New, and click Baseline.

Figure 9 – Create new Baseline for VMware Tools Offline VIB Bundle
The Create Baseline wizard begins. Enter the name of the Baseline, and select Patch as the content type. Click Next.

Figure 10 – Create Baseline Wizard – Step 1
Uncheck the box next to Automatically update this baseline with patches that match the following criteria, and click Next.

Figure 11 – Create Baseline Wizard – Step 2
Filter the patches based on the version of the VMware Tools Offline VIB Bundle that was uploaded, in this case 11.3.

Figure 12 – Create Baseline Wizard – Step 3 (filter)
Select the VMware Tools 11.3.0 Async Release. Be sure to validate the ESXi version to which the bundle applies before making the selection. Click Next.
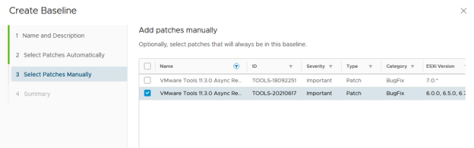
Figure 13 – Create Baseline Wizard – Step 3
Click Finish to create the baseline.
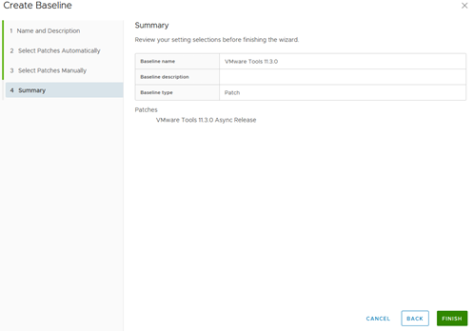
Figure 14 – Create Baseline Wizard – Step 4
Attach Update baseline
Next, choose the vCenter object to which the baseline should be applied. That might be a virtual datacenter, a cluster, or even just a host. Click on the vCenter object to which the baseline should be applied, navigate to Update and Host Updates. Click Attach and click Attach Baseline or Baseline Group.

Figure 15 – Attach Update Baseline
Select the VMware Tools Offline VIB Bundle baseline that was created in the previous step. Click Attach.

Figure 16 – Select Update Baseline to Attach
Remediate Hosts
In the same vCenter view, select the newly attached baseline containing the VMWare Tools Offline VIB Bundle, and click Remediate.
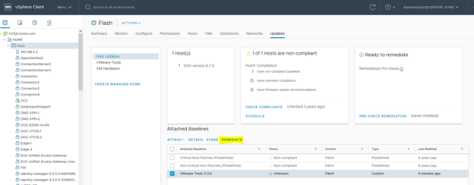
Figure 17 – Remediate Hosts with new Baseline
Select the ESXi hosts to remediate, and click Remediate. There are many options that can be chosen, but none apply in this case.

Figure 18 – Remediate Host Wizard
Update Virtual Machine Tools Version
Now that the VMware Tools version on the host has been updated, the next step is to update VMware Tools on the virtual machines. There are many different approaches to install VMware Tools on a virtual machine. This document mentions four (5) approaches and covers two (2) in detail – not an exhaustive list with excruciating detail.
- Update to Match Host on individual VM using Update Manager
- Update to Match Host on VM Folder using Update Manager
- Update to Match Host on Cluster using Update Manager (not covered here)
- Manually updating individual VMs in vCenter (not covered here)
- Manually running VMware Tools update on VM console (not covered here)
Approach 1 – Update to Match Host on individual VM
With the individual VM selected, go to the Updates view.

Figure 19 – Virtual Machine Tools Update
In the box titled VMware Tools, click Upgrade to Match Host.

Figure 20 – Virtual Machine Tools Update with Update Manager
Select the VM to be updated and review the options under settings.

Figure 21 – Upgrade VMware Tools to Match Host
Review the Scheduling Options to determine when to install VMware Tools on the VM.
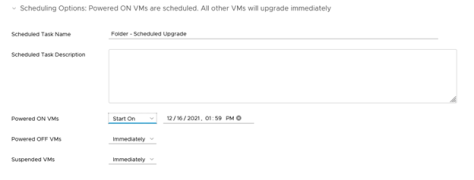
Figure 22 – Scheduling Options
Review the Rollback Options if there is a desire to provide simplified rollback for failed or problematic installations.

Figure 23 – Rollback Options
When all options are reviewed and confirmed, click Upgrade to Match Host

Figure 24 – Upgrade to Match Host
Approach 2 – Update to Match Host on VM Folder
Updates can be applied on the VM folder level. The process follows the same steps as referenced in Approach 1.

Figure 25 – Upgrade to Match Host: Folder containing VMs
Approach 3 – Update to Match Host on Cluster
Updates can be applied on the Cluster level. The process follows the same steps as referenced in Approach 1.
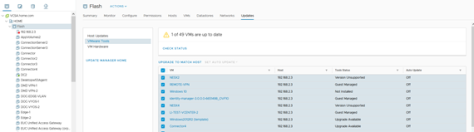
Figure 26 – Upgrade to Match Host: Cluster
Validation
Validation can be performed many ways. On a virtual machine, observe the Tasks view, and confirm a successful Initiated VMware Tools install or upgrade.

Figure 27 – Validation: Virtual Machine Tasks
The Summary view of a virutal machine also shows the VMware Tools build number.

Figure 28 – Validation: Virtual Machine Summary
Click on a VM Folder and the Updates tab – this shows whether the VMs in the selected folder are running a VMware Tools version that is Up to Date.

Figure 29 – Validation: VM Folder – Updates View
Click on a virtual datacenter, go to the VMs tab, and list the VMware Tools Version Status, which will show the build number.

Figure 30 – Validation: Virtual Datacenter – Virtual Machine Inventory
Click on a Cluster, go to the Updates tab – this shows whether the VMs in the selected cluster are running a VMware Tools version that is Up to Date.

Figure 31 – Validation: Cluster – Updates View