Many security organizations now require that TLS 1.1 be disabled on web servers. One area that gets overlooked are load balancers that are configured for SSL Offload or SSL Termination. One use case where I have customers using SSL termination on NSX-T native load balancing for web servers is where, in a one-arm configuration, the application owner has a requirement to see the client IP address in the logs. This is achieved by inserting the X-Forwarded-For header (XFF). In order to insert the XFF header, SSL must be terminated on the load balancer, thus a L7 virtual server is required. Below is a screenshot of where the Client SSL Profile is configured on the L7 Virtual Server. The screenshot shows the use of the default-balanced-client-ssl-profile.

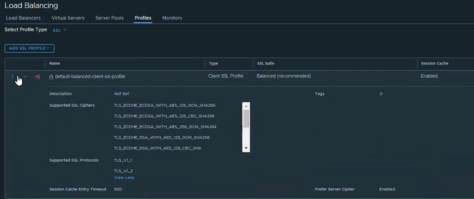
In order to take a closer look at the SSL profiles on the NSX-T native load balancer, navigate to Load Balancing | Profiles and in Select Profile Type, choose SSL.

Open the arrow next to default-balanced-client-ssl-profile to view the SSL Ciphers and SSL Protocols supported by the profile. As we can see, TLS 1.1 is listed as supported.
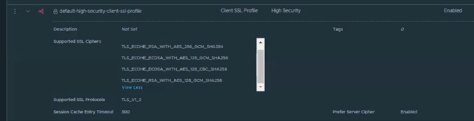
Looking at default-high-security-client-ssl-profile we can see that the only supported SSL Protocol is TLS 1.2. Choosing the default-high-security-client-ssl-profile is the easiest to eliminate TLS 1.1.
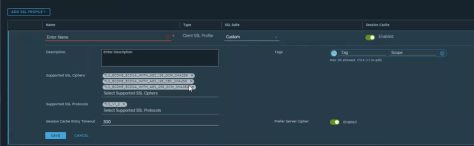
In some cases, the security department will call out specific ciphers that they want to disallow. In that case, the best option is to create a custom Client SSL Profile. Creation is shown in the screenshot below.

First, select Custom under SSL Suite. Then, modify the SSL Suite removing TLS 1.1. Finally, remove any unnecessary SSL Ciphers. Click Save.